HTB Paper
Start with enumeration
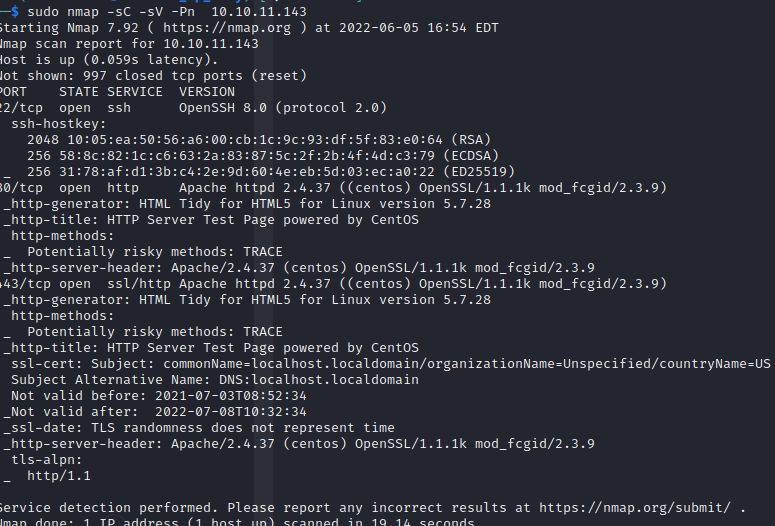
sudo nmap -sV -sC -Pn -p- MACHINEIP
 Ports:
Ports:
1
2
3
4
22, running ssh 8.0
80, runnig Apache 2.4.37
443, ssl/http Apache htmld 2.4.37
are open
navigate to the webpage
We land on an Apache default page
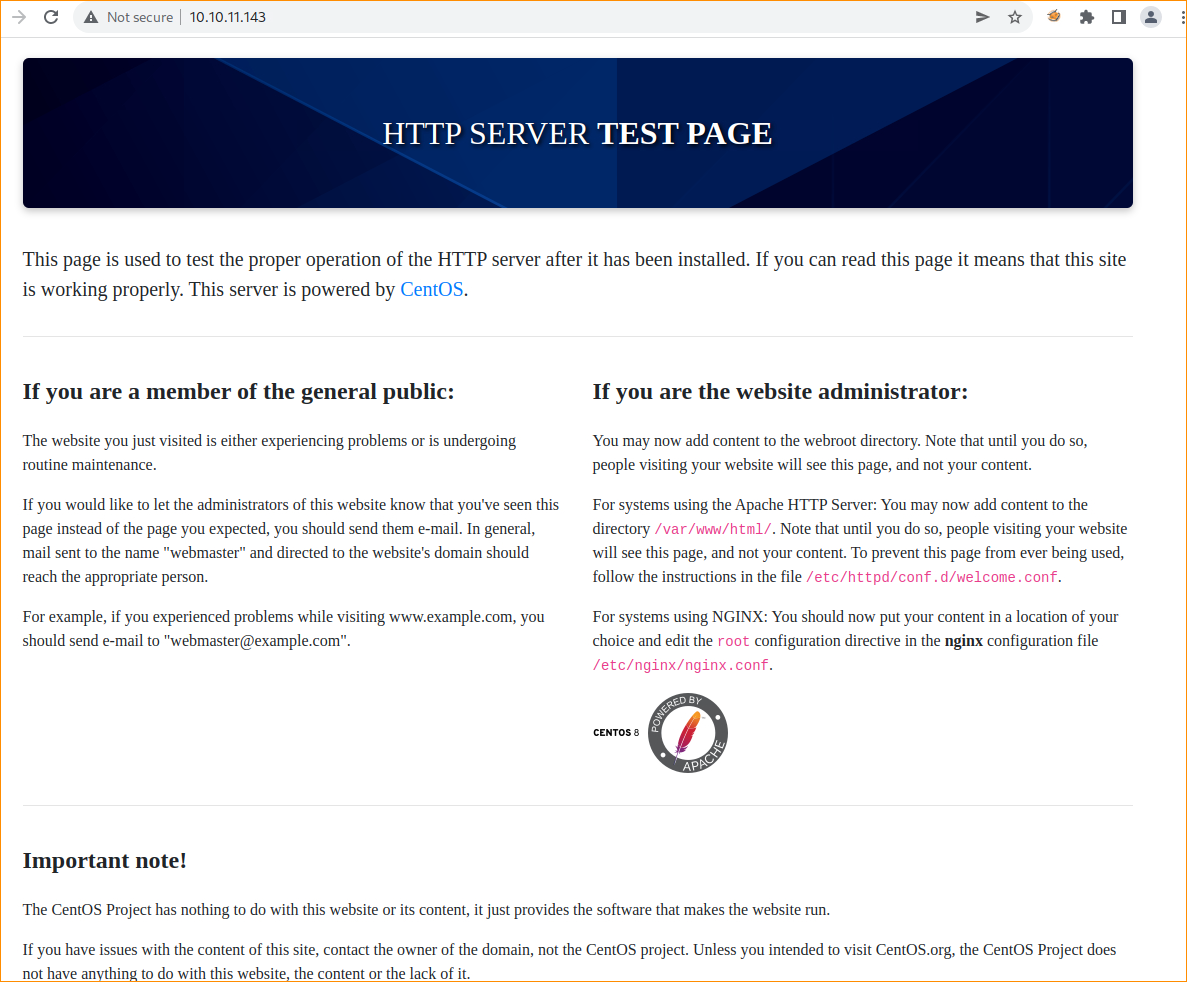
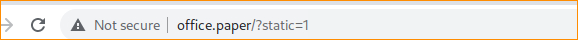
After using the inspection > NETWORK>refresh page, we find the header office.paper
This can also be achieved with burpsuite
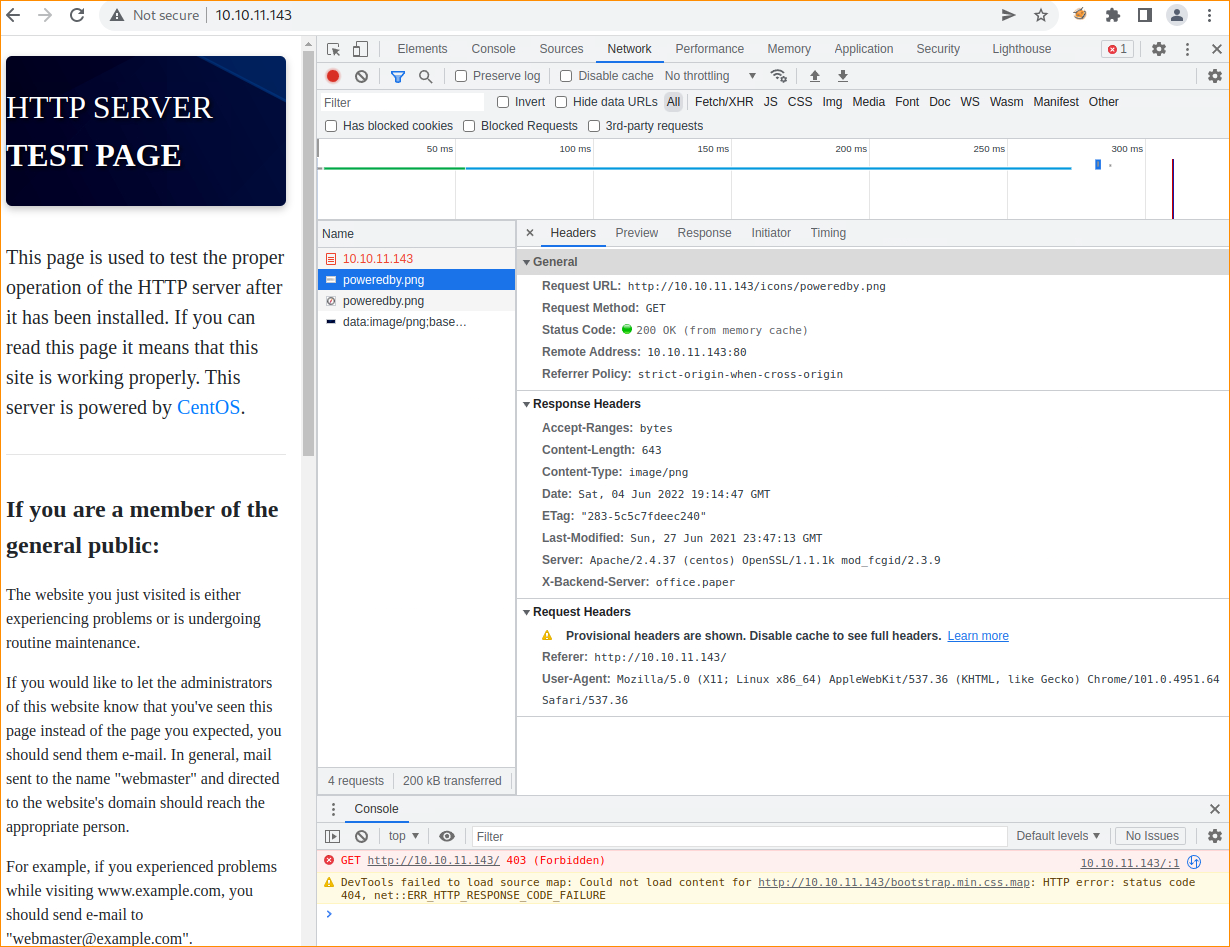 Lets add this to /etc/hosts
Lets add this to /etc/hosts
 Its a WordPress blog.
Running [[wordpress wpscan]] brought no results
Its a WordPress blog.
Running [[wordpress wpscan]] brought no results
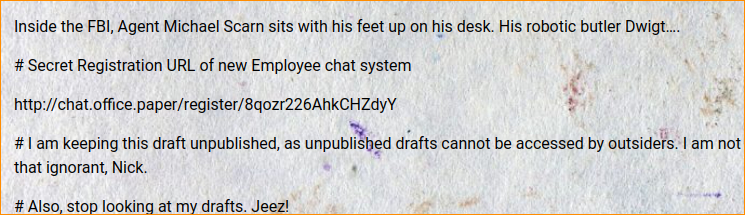
Use exploit ?static=1 at the end of the dns address to reach a vulnerable page
After some reading, we find a link for a chat room
Lets add this to our hosts as well

navigate to the secret page, register, and log in

Get a conversation started with dwights bot.
RESPOND_TO_EDITED=trueROCKETCHAT_USER=recyclopsLANG=en_US.UTF-8OLDPWD=/home/dwight/hubotROCKETCHAT_URL=http://127.0.0.1:48320ROCKETCHAT_USESSL=falseXDG_SESSION_ID=1USER=dwightRESPOND_TO_DM=truePWD=/home/dwight/hubotHOME=/home/dwightPORT=8000ROCKETCHAT_PASSWORD=Queenofblad3s!23SHELL=/bin/shSHLVL=4BIND_ADDRESS=127.0.0.1LOGNAME=dwightDBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/1004/busXDG_RUNTIME_DIR=/run/user/1004PATH=/home/dwight/hubot/node_modules/coffeescript/bin:node_modules/.bin:node_modules/hubot/node_modules/.bin:/usr/bin:/bin_=/usr/bin/cat
Queenofblad3s!23
As I always say, “Hack, Sleep, Repeat”